Microsoft Cybercrime Unit is a group operating in Redmond WA, fighting various cyberthreats in collaboration with the American government and foreign agencies. The threats they address range from counterfeiting to child trafficking networks, to botnet herding. So, what is a botnet?
According to Wikipedia:
"A botnet is a number of Internet-connected computers communicating with other similar machines in which components located on networked computers communicate and coordinate their actions by command and control (C&C) or by passing messages to one another (C&C might be built into the botnet as P2P).[1] Botnets have been used many times to send spam email or participate in distributed denial-of-service attacks. The word botnet is a combination of the words robot and network. The term is usually used with a negative or malicious connotation."

Because of the pervasiveness of Windows products, Microsoft has been in a privileged position to address the threats caused by botnets. The DCU is based in Minority-Report-like offices, where investigators track online "bad guys" day and night from an evidence room. In an effort to communicate these efforts to the general public, they commissioned the Office for Creative Research to visualize botnet data.
Botnet activity across the world — Microsoft DCU

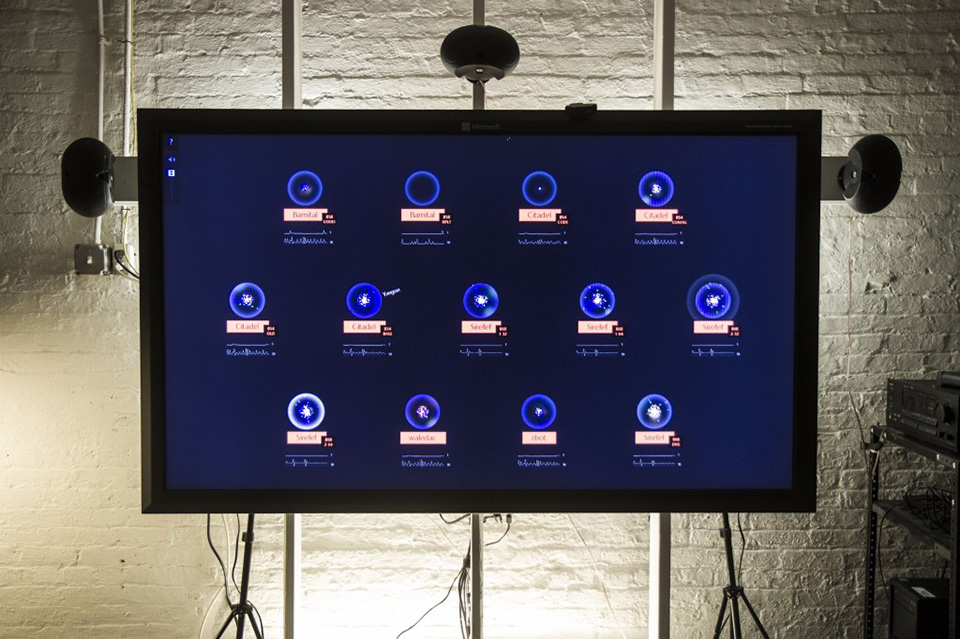
With this project, the Office for Creative Research was tasked to build an installation piece that would live in DCU's main space. It had to create a data visualization that would communicate botnet data in a creative, engaging way.
We set out to create an interactive piece that would not only show the inherent beauty of these complex systems, but also become a useful tool for researchers to explore botnets' organic behaviors.
The Cybercrime Center in Microsoft's headquarters — Microsoft DCU